Frida & Objection | Bypass ssl pinning of android
Statement.
Any direct or indirect consequences and losses a result of the dissemination or use of the information provided in this article shall be the responsibility of the user himself, and Raytheon and the author of the article shall not be liable for this.
Raytheon has the right to modify and interpret this article. To reproduce or disseminate this article, the integrity of the article, including copyright notices, must be guaranteed. The content of this article may not be arbitrarily modified or subtracted without the permission of Raytheon, and it may not be used for commercial purposes in any way.
Objective.
Problem:
When you grab a package, you install a burp suite CA certificate, but sometimes the app can't catch https traffic when it doesn't trust a third party to issue the certificate.
Some people abroad try 4 MITM intermediaries to modify the flow method:
Custom CA added to trusted certificate store (only for Android 6.0 and below)
Custom CA certificate overwriting packaging (overwriting UniversalRootCA certificate with custom CA with apk studio)
frida hook and bypass the ssl certificate check
Reverse custom certificate code
At this point, try SSL Pinning, bypass validation, and you need the code for the hook application.
Method one SSL pinning bypass
1. Using the simulator, rooted, android version is 6.0
The following example is a simplified version of the Frida JavaScript script:
var so = Java.use("o.so");
so.a.overload().implementation = function(){
}
Hijacks the method and always returns it to true.
2. Attempts to bypass SSL fixation are based on SSLContext operations
Port SSL Pinning Java code to Frida JavaScript.
1. Load our malicious CA certificate from the device
2. Create your own KeyStore that contains trusted CA
3. Create a TrustManager that trusts CA in our KeyStore
When the application initialized its SSLContext, we hijacked the SSLContext.init() method and called itThe second argument(i.e. Application TrustManager)And.We had prepared our own TrustManager exchange。(SSLContext.init(KeyManager,TrustManager,SecuRandom))。
In this way, we basically re-pin the application to our own CA!
1.导出burp suite,CA证书,cert-der.cer
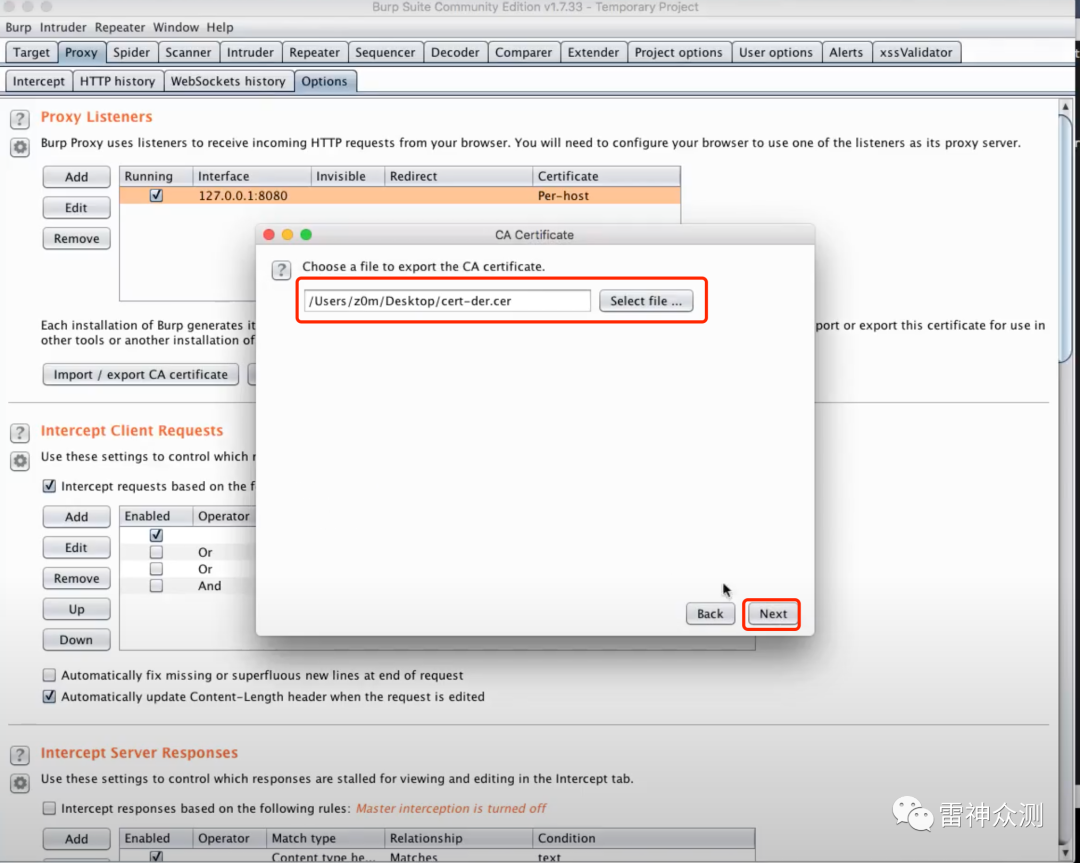
2. Upload cer-der.cer to the simulator
adb push /Users/z0m/Desktop/cert-der.cer /data/local/
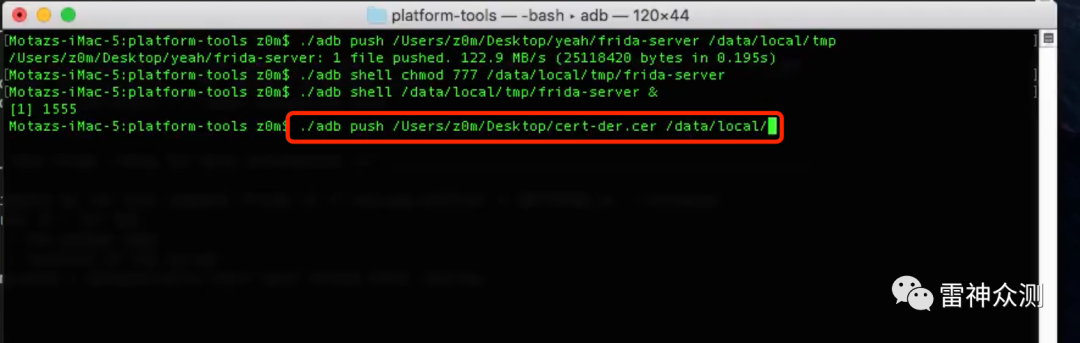
保存成fried-android-repinning.js
/*Android SSL Re-pinning frida script v0.2 030417-pier$ adb push burpca-cert-der.crt /data/local/tmp/cert-der.crt$ frida -U -f it.app.mobile -l frida-android-repinning.js --no-pausehttps://techblog.mediaservice.net/2017/07/universal-android-ssl-pinning-bypass-with-frida/UPDATE 20191605: Fixed undeclared var. Thanks to @oleavr and @ehsanpc9999 !*/setTimeout(function(){Java.perform(function (){console.log("");console.log("[.] Cert Pinning Bypass/Re-Pinning");var CertificateFactory = Java.use("java.security.cert.CertificateFactory");var FileInputStream = Java.use("java.io.FileInputStream");var BufferedInputStream = Java.use("java.io.BufferedInputStream");var X509Certificate = Java.use("java.security.cert.X509Certificate");var KeyStore = Java.use("java.security.KeyStore");var TrustManagerFactory = Java.use("javax.net.ssl.TrustManagerFactory");var SSLContext = Java.use("javax.net.ssl.SSLContext");// Load CAs from an InputStreamconsole.log("[+] Loading our CA...")var cf = CertificateFactory.getInstance("X.509");try {var fileInputStream = FileInputStream.$new("/data/local/tmp/cert-der.crt");}catch(err) {console.log("[o] " + err);}var bufferedInputStream = BufferedInputStream.$new(fileInputStream);var ca = cf.generateCertificate(bufferedInputStream);bufferedInputStream.close();var certInfo = Java.cast(ca, X509Certificate);console.log("[o] Our CA Info: " + certInfo.getSubjectDN());// Create a KeyStore containing our trusted CAsconsole.log("[+] Creating a KeyStore for our CA...");var keyStoreType = KeyStore.getDefaultType();var keyStore = KeyStore.getInstance(keyStoreType);keyStore.load(null, null);keyStore.setCertificateEntry("ca", ca);// Create a TrustManager that trusts the CAs in our KeyStoreconsole.log("[+] Creating a TrustManager that trusts the CA in our KeyStore...");var tmfAlgorithm = TrustManagerFactory.getDefaultAlgorithm();var tmf = TrustManagerFactory.getInstance(tmfAlgorithm);tmf.init(keyStore);console.log("[+] Our TrustManager is ready...");console.log("[+] Hijacking SSLContext methods now...")console.log("[-] Waiting for the app to invoke SSLContext.init()...")SSLContext.init.overload("[Ljavax.net.ssl.KeyManager;", "[Ljavax.net.ssl.TrustManager;", "java.security.SecureRandom").implementation = function(a,b,c) {console.log("[o] App invoked javax.net.ssl.SSLContext.init...");SSLContext.init.overload("[Ljavax.net.ssl.KeyManager;", "[Ljavax.net.ssl.TrustManager;", "java.security.SecureRandom").call(this, a, tmf.getTrustManagers(), c);console.log("[+] SSLContext initialized with our custom TrustManager!");}});},0);
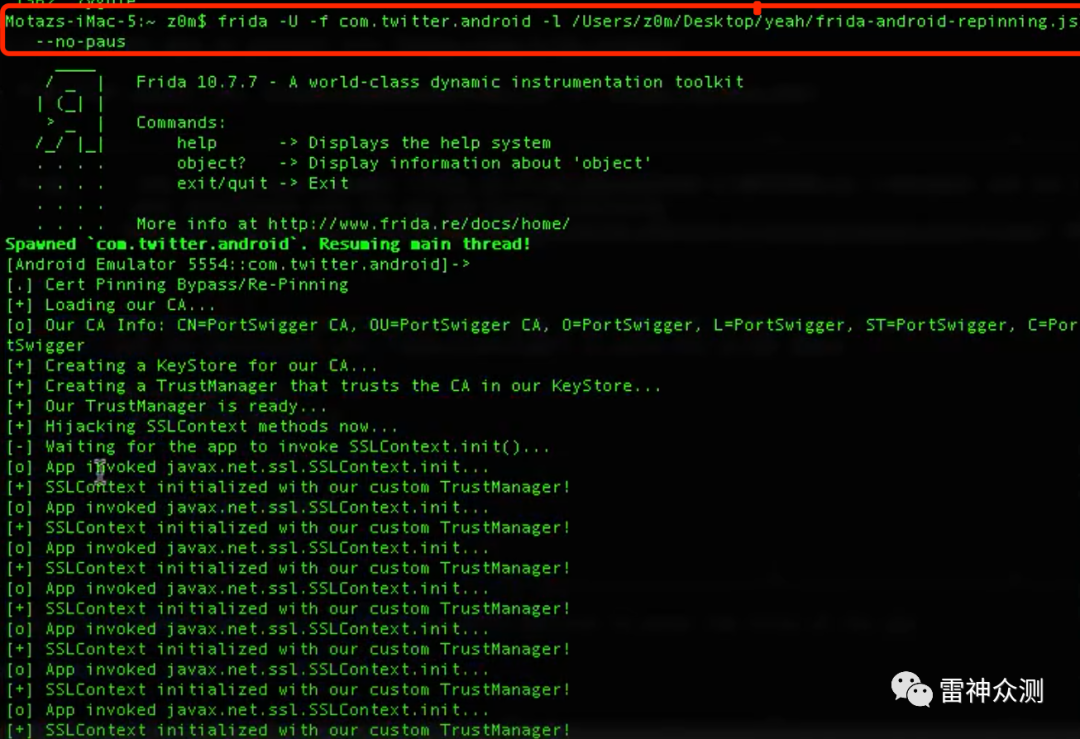
3. Run frida crawl twitter
frida -U -f com.twitter.android -l /usr/z0m/Desktop/yeah/frida-android-repinning.js --no-paus
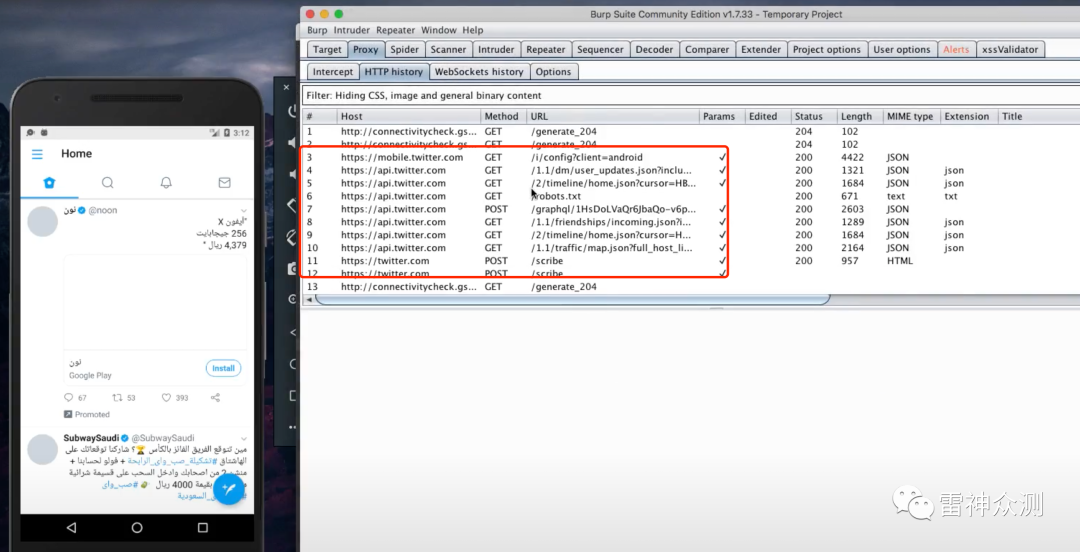
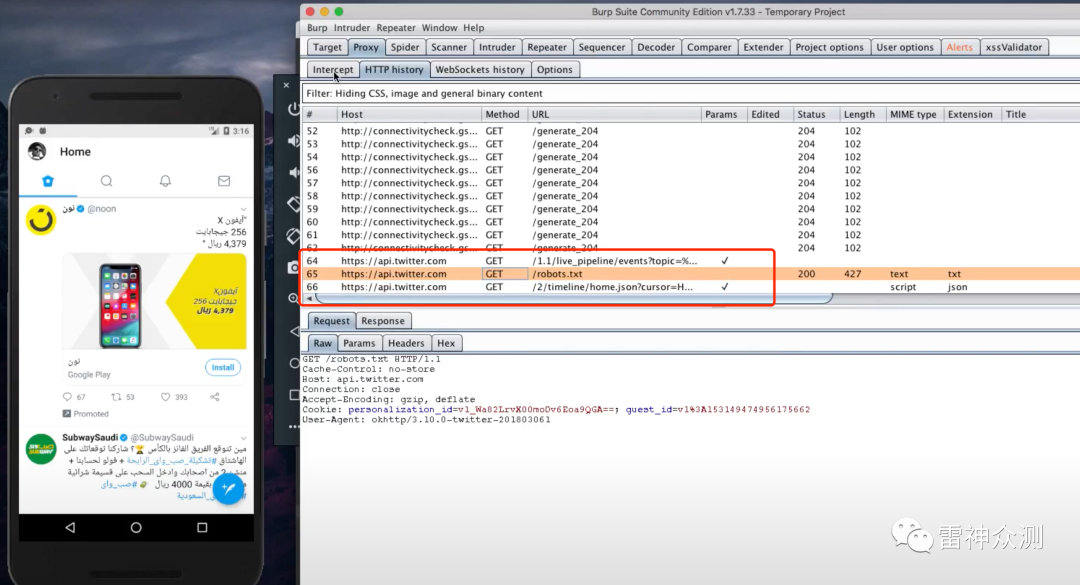
4. Grab the https bag
Method two objection SSL pinning
Objection is a Frida-based tool that makes it easy for us to find out directly the methods in apk that require HOOK, as well as agree on function parameters, return values, stack calls, and so on.
How to use:
https://blog.csdn.net/qq_40827990/article/details/106347852
Source:
https://github.com/sensepost/objection/
$Objection -g com.twitter.android explore
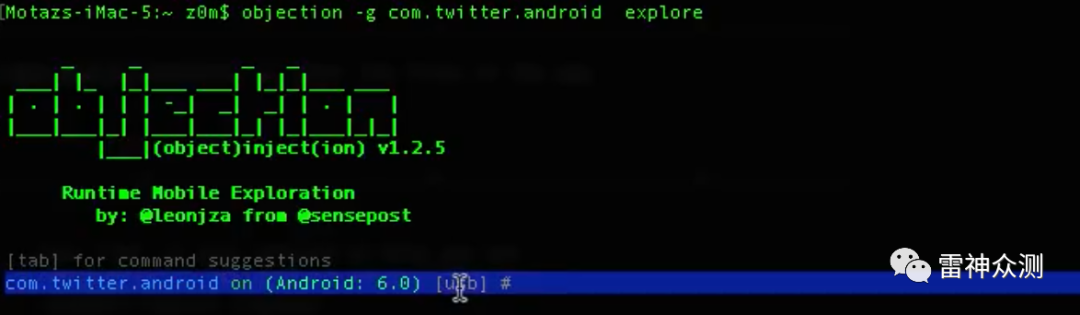
android hooking list classes
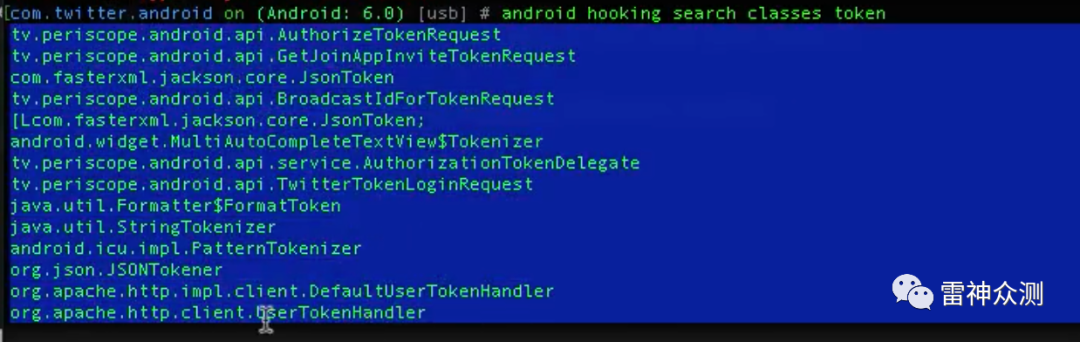
android hooking search classes
token
android sslpinning disable
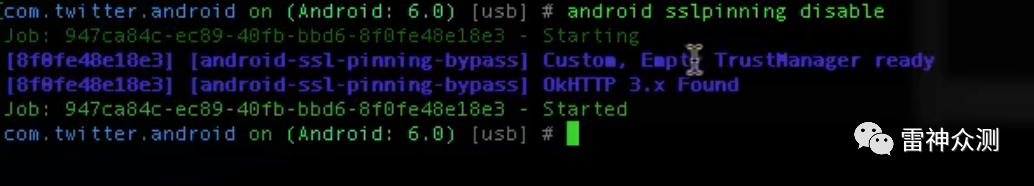
Grab https traffic
Recruitment
An HengLei God Test SRC Operations (Interns)
————————
Description of Responsibilities
1. Responsible for the operation of new media on SRC's microblogging and WeChat public numbers, to maintain user activity and improve site visits;
2. Responsible for the white hat submission loophole audit, Rank rating, vulnerability repair and other related communication work, to promote friendly and collaborative communication between auditors and white hat;
3. Participate in the planning, organization and implementation of offline activities for white hats, such as salons, press conferences, technical exchange forums, etc.;
4. Actively participate in the brand promotion work of Raytheon, to assist technical personnel to export high-quality technical articles;
5. Actively participate in the company's media, industry-related media and other market resources to work and communicate.
"Requirements for appointment"
1. Strong sense of responsibility, lively personality, with good interpersonal skills;
2. Interested in network security and have a basic understanding of the industry;
3. Good case writing and activity organization and coordination skills.
The resume is posted to the strategy@dbappsecurity.com.cn
Designer (Intern)
————————
Job Description
Responsible for the design company's daily promotional pictures, soft text and other design-related work, responsible for product brand design.
Job Requirements
1, engaged in graphic design-related work for more than 1 year, familiar with the printing process, with keen observation and aesthetic ability, and excellent creative design ability, VI design, advertising design, picture book design and other expertise;
2, have a good artistic background, aesthetic ability and creativity, strong sense of color;
3, brand communication, product design or new media visual work experience;
Additional information about the position
Name: Hangzhou Anheng Information Technology Co., Ltd
Office location: 19th floor of Anheng Building, Riverside District, Hangzhou City
Education requirements: undergraduate and above
Years of service: 1 year or more, conditions can be relaxed
The resume is posted to the strategy@dbappsecurity.com.cn
Secure recruitment
————————
Company: Anheng Information
Post:Web security security researcher
Department: Strategic Support
Salary: 13-30K
Years of service: 1 year plus
Location: Hangzhou (headquarters), Guangzhou, Chengdu, Shanghai, Beijing
Working environment: a building, fitness venues, doctors, handsome guys, beautiful women, high-level canteen...
Job Responsibilities
1. Regularly for the department, the company-wide technology sharing;
2. Cutting-edge attack and defense technology research, tracking the security dynamics in the field of security at home and abroad, vulnerability disclosure and landing precipitation;
3. Responsible for the completion of department penetration testing, red and blue confrontation business;
4. Responsible for the construction of automation platform
5. Responsible for testing and landing bypass scheme for common WF product rules
Job Requirements
1. At least 1 year of experience in the field of safety;
2. Familiar with HTTP protocol-related technologies
3. Have large-scale products, CMS, vendor vulnerability cases;
4. Master the basics of php, java, asp.net code audit (one or more)
5. Master web Fuzz fuzzy testing vulnerability mining technology
6. Master the principle of OWASP TOP 10 security vulnerability and familiar with the exploit method
7. Have independent analysis of vulnerability experience, familiar with a variety of Web debugging skills
8. Familiarize yourself with at least one of the common programming languages (Asp.net, Python, php, java)
(Plus item)
1. Have good English document reading ability;
2. Has participated in the technology salon as a guest for technology sharing;
3. With CISSP, CISA, CSSLP, ISO27001, ITIL, PMP, COBIT, Security, CISP, OSCP and other security-related qualifications;
4. With large SRC vulnerability submission experience, access to annual recognition, large-scale CTF winners;
5. Developed security-related open source projects;
6. People with good interpersonal communication, coordination, analysis and problem solving skills are preferred;
7. Personal Technology Blog;
8. Contribute articles in high-quality communities;
Post:Security Red Team Weapon Automation Engineer
Salary: 13-30K
Years of service: 2 years plus
Location: Hangzhou (Headquarters)
Job Responsibilities
1. Responsible for the weaponization landing and research in red and blue confrontation;
2. Platform construction;
3. Safety research landing.
Job Requirements
1. Skilled use of at least one language, such as Python, java, c/c, as the main development language;
2. Skilled use of Django, flask and other common web development frameworks, as well as skilled use of mysql, mongoDB, redis and other data storage programs;
3: familiar with domain security and intranet horizontal penetration, common web and other vulnerability principles;
4. Have a strong interest in security technology and enthusiasm, have subjective research and learning motivation;
5. Have positive values, good teamwork ability and strong problem solving ability, good at communication, willing to share.
(Plus item)
1. High-level tcp services, distributed and other relevant experience is preferred;
2. Open source security products are preferred on github;
3: Have experience in security development, have analyzed relevant open source security tools alone, and participated in the development of relevant post-penetration framework and other priorities;
4. Sharing relevant technical articles on security platforms such as freebuf, security guests and prophets is preferred;
5. Have good English document reading ability.
The resume is posted to the strategy@dbappsecurity.com.cn
Post:Red Team Weaponized Golang Development Engineer
Salary: 13-30K
Years of service: 2 years plus
Location: Hangzhou (Headquarters)
Job Responsibilities
1. Responsible for the weaponization landing and research in red and blue confrontation;
2. Platform construction;
3. Safety research landing.
Job Requirements
1. Master at least one language, such as C/C?/Java/Go/Python/JavaScript, as the main development language;
2. Skilled use of Gin, Beego, Echo and other common web development framework, familiar with MySQL, Redis, MongoDB and other mainstream database structure design, independent deployment tuning experience;
3. Understand docker, can carry out simple project deployment;
3. Be familiar with the principles of common web vulnerabilities and be able to write the corresponding utilization tools;
4. Be familiar with the basic operating principles of TCP/IP protocol;
5. Have a strong interest and enthusiasm in security technology and development technology, have subjective research and learning motivation, have positive values, good teamwork ability and strong problem solving ability, good at communication, willing to share.
(Plus item)
1. High-level tcp services, distributed, message queues and other relevant experience is preferred;
2. Open source security products are preferred on github;
3: Have experience in security development, have analyzed relevant open source security tools alone, and participated in the development of relevant post-penetration framework and other priorities;
4. Sharing relevant technical articles on security platforms such as freebuf, security guests and prophets is preferred;
5. Have good English document reading ability.
The resume is posted to the strategy@dbappsecurity.com.cn
Focus on penetration testing techniques
The world's latest cyberattack technology
END

Go to "Discovery" - "Take a look" browse "Friends are watching"